21/tcp: Allows FTP (File Transfer Protocol) which is used for file transfers
22/tcp: Allows SSH (Secure Shell) for secure remote connections
80/tcp: Allows HTTP (HyperText Transfer Protocol) for general web browsing
443/tcp: Allows HTTPS (HyperText Transfer Protocol Secure) for encrypted web sites
888/tcp: This port is arbitrary (may be used for specific services or applications)
39000:40000/tcp: Range of allowed ports (May be used for applications that require a large number of ports)
25581/tcp: This port is also custom.
The (v6) means that traffic is allowed from IPv6, the newer version of IP addressing. The ones without (v6) are IPv4, the older version of IP addressing.
If you want to delete or modify these rules, you can use the following commands:
Delete a rule (e.g. delete port 888):
sudo ufw delete allow 888/tcp
Deny a port (e.g. deny port 21):
sudo ufw deny 21/tcp
Check the status of UFW rules:
sudo ufw status
If you need more advice on managing UFW firewall rules or other settings, feel free to ask!
Managing UFW firewall rules or other settings For security
Managing UFW (Uncomplicated Firewall) rules is one of the simplest and most effective ways to enhance the security of your server or computer. It allows you to control access to the ports used on your system and your internet connection. Here’s how to manage UFW rules to enhance security
- Enable UFW
If UFW is not enabled, you can enable it with the following command:
sudo ufw enable - Once enabled, UFW will start and start protecting your system from unauthorized connections.
- Check the status of UFW
To see what rules are set and the status of the firewall:
sudo ufw status verbose - This command will show you all the details about the enabled rules, including the allowed ports and firewall settings.
- Only allow access to the necessary ports.
Allowing the ports necessary for the application to work, such as HTTP (80), HTTPS (443), or SSH (22), is a good way to restrict access:
Allow SSH to connect remotely (if using SSH):
sudo ufw allow ssh
Allow HTTP and HTTPS for the web server:
sudo ufw allow http
sudo ufw allow https
Require only certain IPs to connect, such as allowing specific IPs from your machine:
sudo ufw allow from to any port 22
- Deny access to unnecessary ports
If a port is not necessary on your system, You should disable access by denying:
Deny FTP port (21) or unused ports:
sudo ufw deny 21/tcp
Disable access to potentially vulnerable ports, such as MySQL or MongoDB, that are not used externally:
sudo ufw deny 3306/tcp # for MySQL
sudo ufw deny 27017/tcp # for MongoDB
- Set automatic access blocking (Rate Limiting)
Blocking attacks that attempt to access the system multiple times can be done by limiting the access rate (Rate Limiting):
Set connection limit for SSH (prevents brute force attacks):
sudo ufw limit ssh
- Set general access blocking
If you don’t want to allow connections from everywhere You can set a rule to block connections from everywhere and allow only the necessary ones:
Block access from everywhere:
sudo ufw default deny incoming
Allow outgoing connections:
sudo ufw default allow outgoing
- Blocking connections from unwanted IPs
If you want to block access from specific IPs or IP ranges:
Block specific IPs:
sudo ufw deny from Block IP ranges:
sudo ufw deny from to
- Reset all rules
To reset all settings and start over:
sudo ufw reset
- Review rules regularly
You should review UFW rules periodically to make sure no unnecessary ports or accesses are open. Or it could be due to misconfiguration:
sudo ufw status numbered
Then you can delete unnecessary rules by using the rule number:
sudo ufw delete
Caution
Do not open unused ports: Only open ports that are necessary for the application to function.
Be careful with vulnerable ports: Some ports (e.g. 21/FTP) can be vulnerable to attack.
Do not open SSH to everyone: SSH connections should be restricted by using rules that allow only trusted IPs.
Good configuration and regular monitoring will help protect your system from threats from external networks.
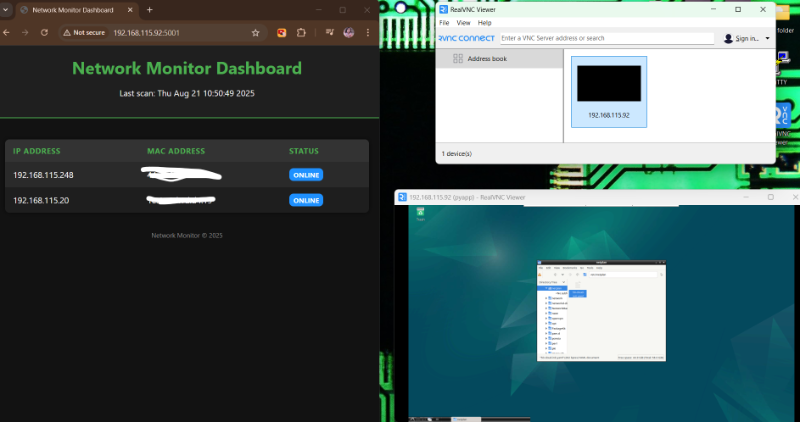
The website design looks great—clean, user-friendly, and visually appealing! It definitely has the potential to attract more visitors. Maybe adding even more engaging content (like interactive posts, videos, or expert insights) could take it to the next level. Keep up the good work!